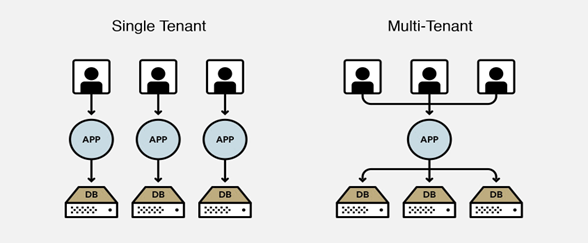
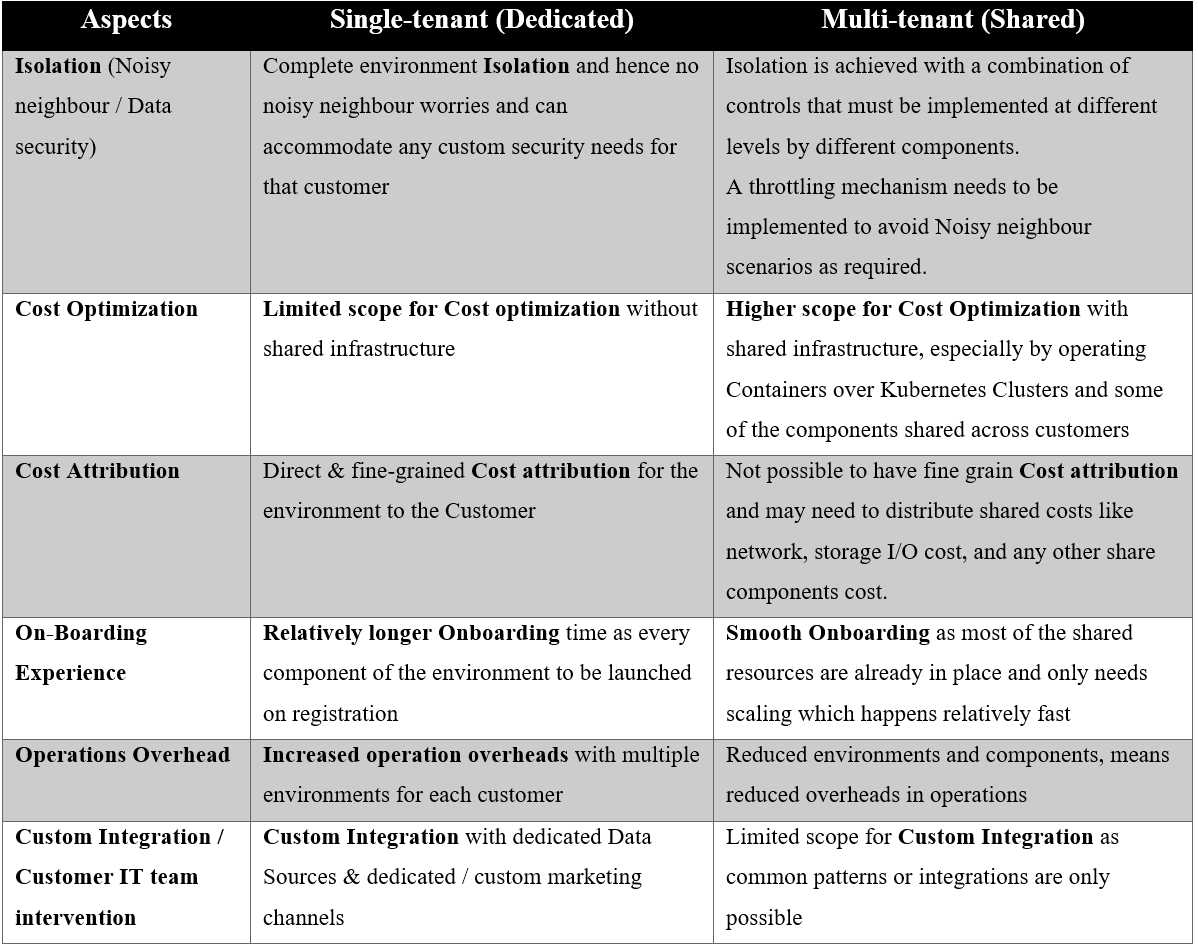
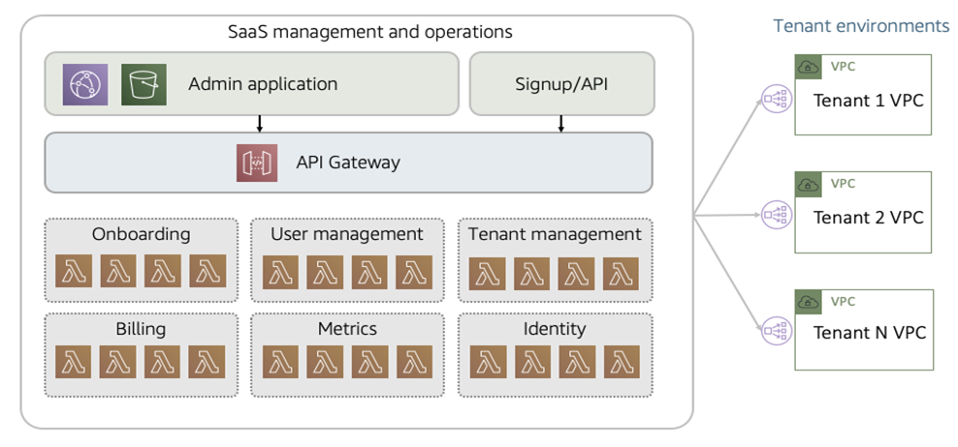
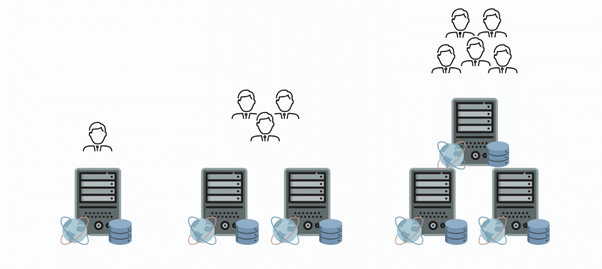
For businesses looking for accessibility, functionality, and adaptability in a competitive business environment, software-as-a-service (SaaS) is becoming an increasingly attractive option. SaaS is a software distribution model that provides businesses with a lot of flexibility and cost-effectiveness, making it a very dependable choice for many business models and industries. Due to its ease of use, user accessibility, security, and widespread connectivity, it has become popular among many businesses. The industry is seeing a trend in more ISVs enabling their products to be SaaS-ready and even more so with the acceptance of HyperCloud paving the way for affordable connectivity across the globe.
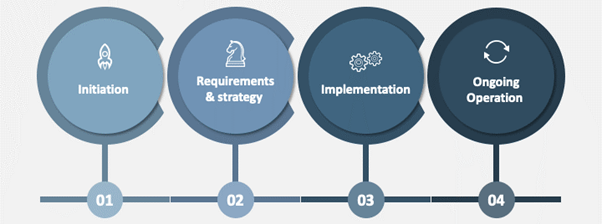
If you are an ISV looking for a cloud solution, then this blog will walk you through the various considerations and support features offered with a SaaS Factory approach for Architecture and Design.