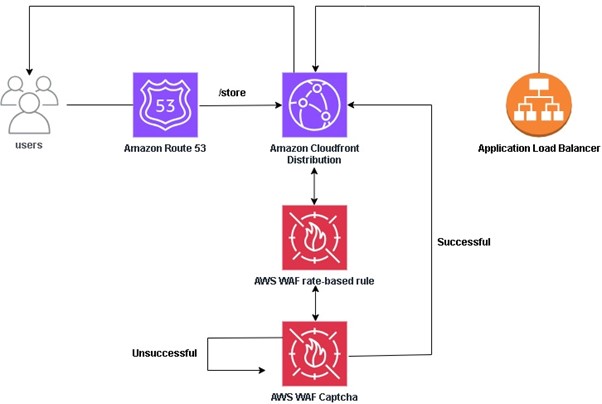
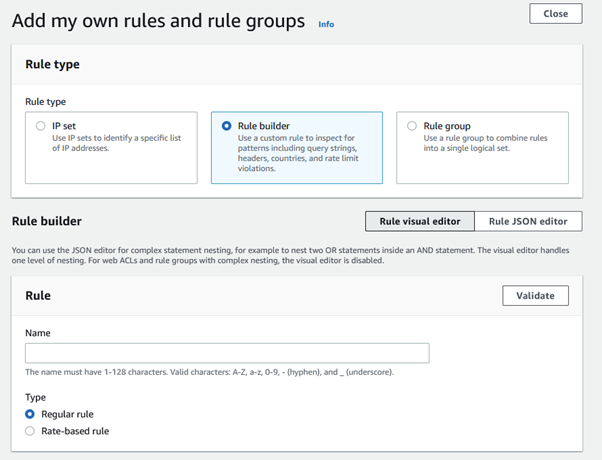
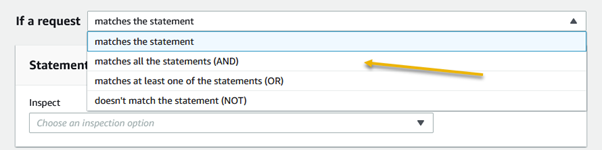
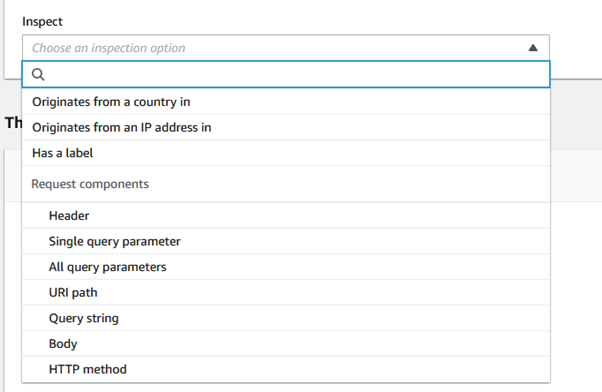
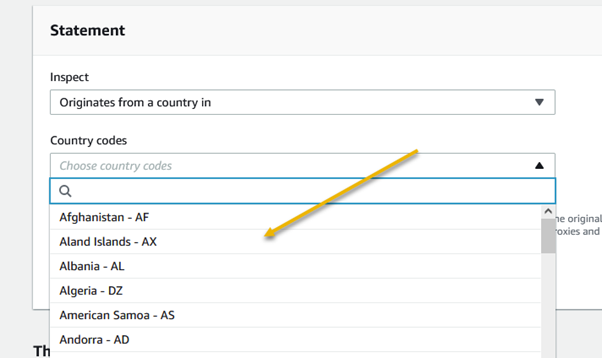
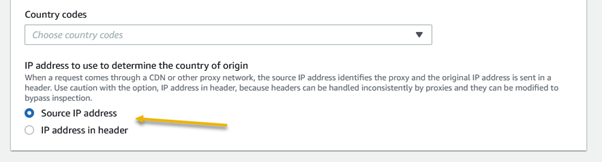
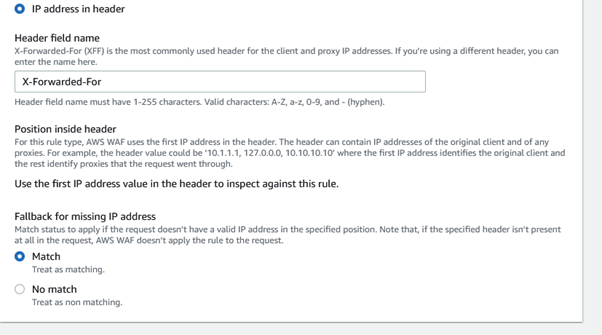
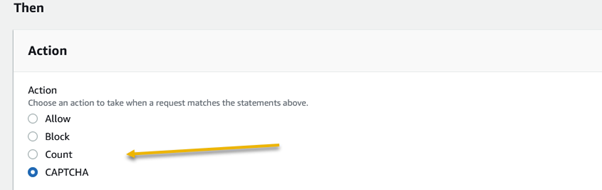
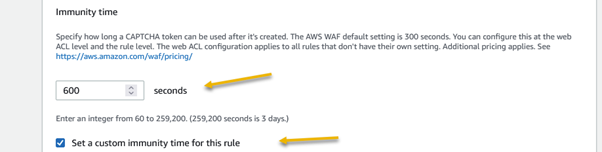
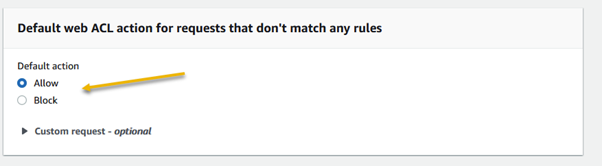
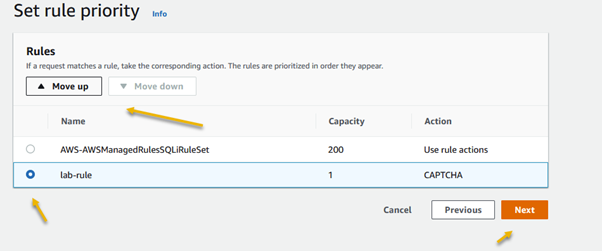
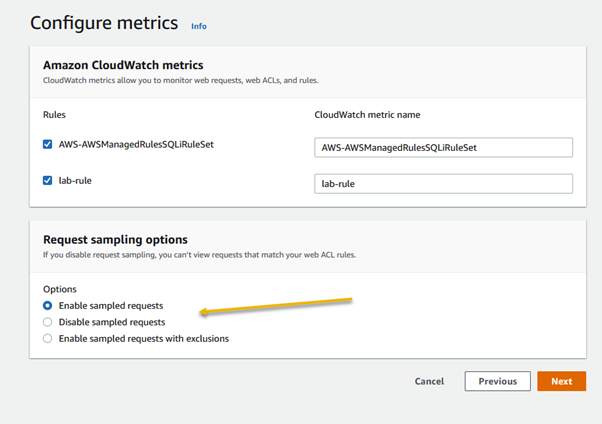
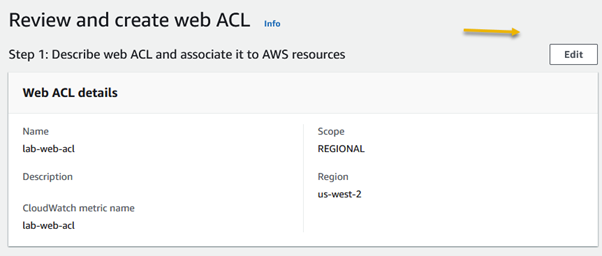
Amazon Web Services (AWS) equips businesses with a myriad of tools and guidance to tackle the ever-growing menace of bot traffic on their websites. Web applications face threats from various vectors like cross-site scripting, SQL injection, path traversal, local file inclusion, and distributed denial-of-service (DDoS) attacks.
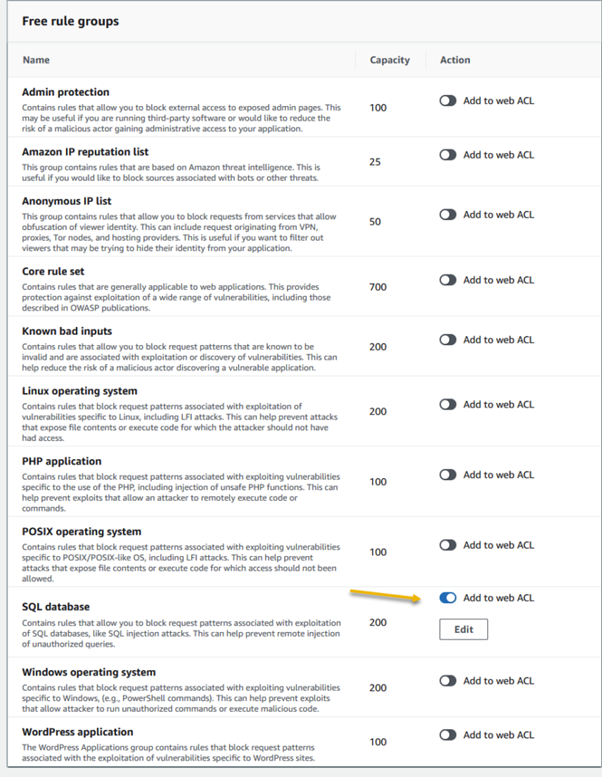
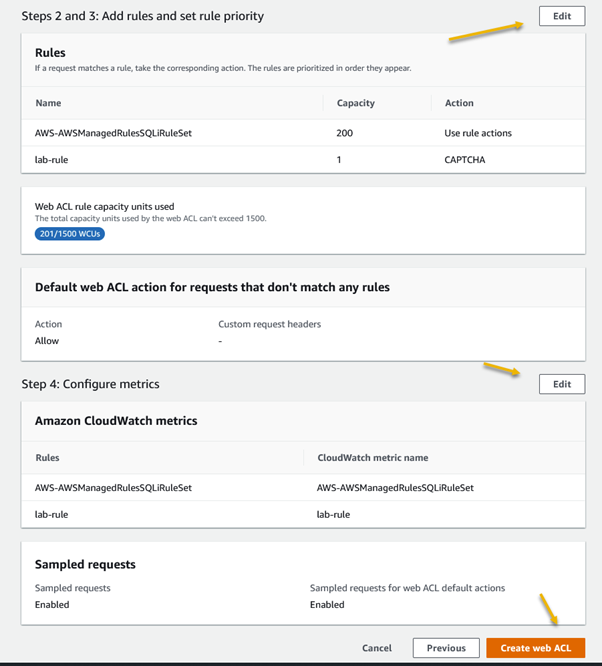
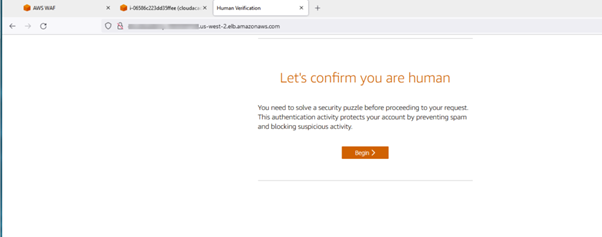
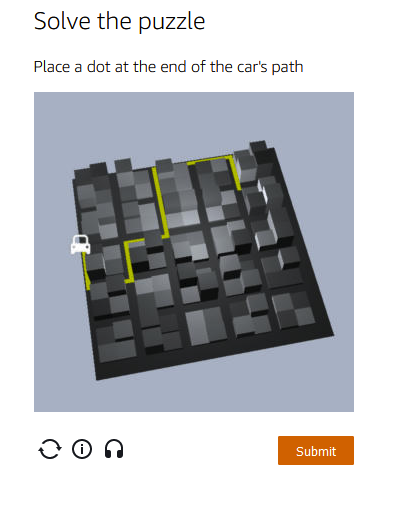
AWS WAF emerges as a powerful solution, offering meticulously crafted managed rules. These rules act as a shield, providing robust protection against prevalent application vulnerabilities and undesirable web traffic, all without the need for businesses to develop their own rules. The result is a fortified web security posture with minimal implementation hassle.