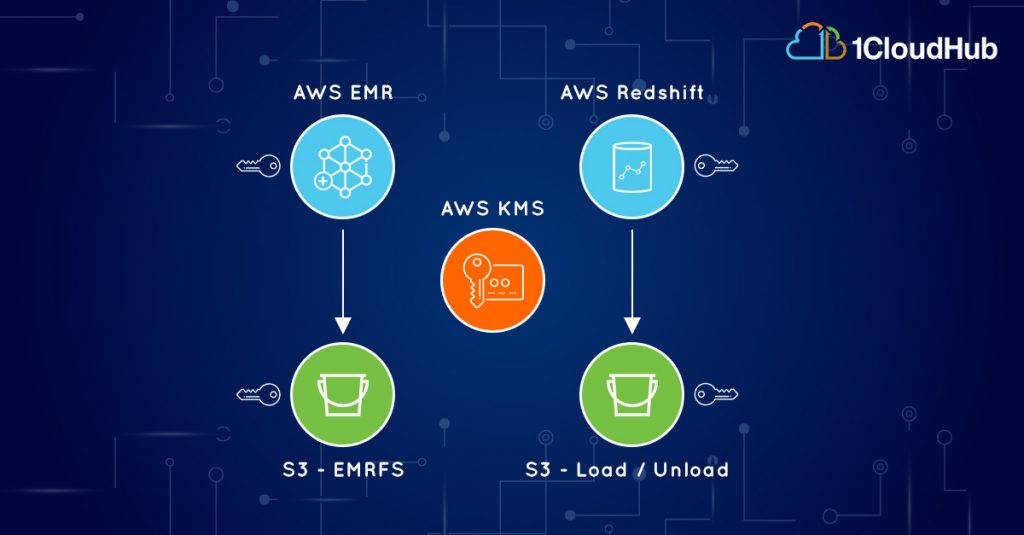
Data security is one of the key factors in cloud decision for enterprises, especially those that are handling their customer’s data under SLA. Today’s cloud services do have standard security as the default option that is quick and simple to implement. But when it comes to leveraging cloud for Big Data processing, customer’s information security teams are keen to ensure that they have the best custom controlled data protection possible on top of the mechanisms available as default options.
One of our customers who was running their Hadoop data processing on IaaS, to process high-velocity streaming data from IoT devices engaged us for architecting a PaaS based solution.