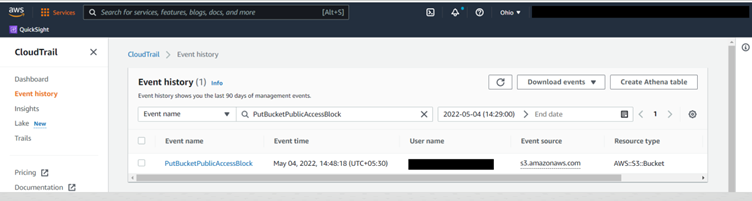
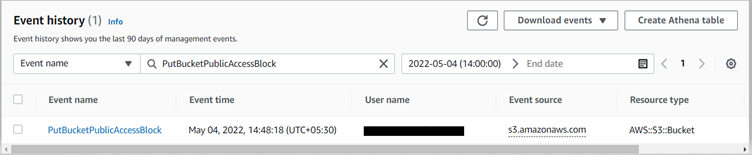
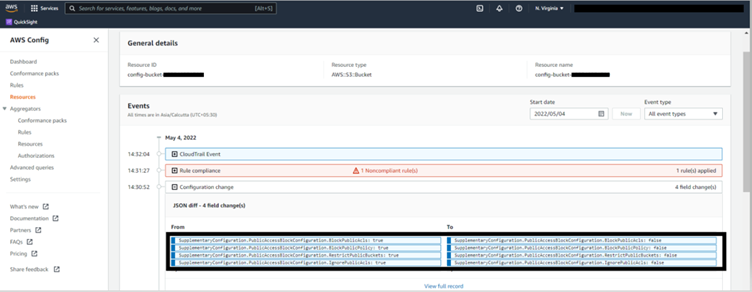
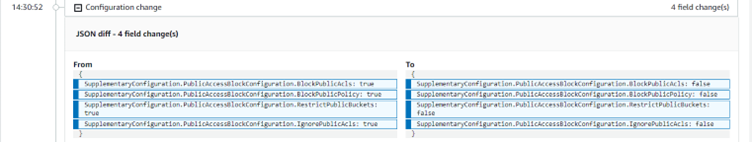
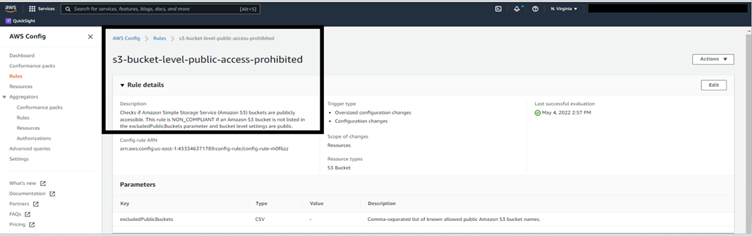
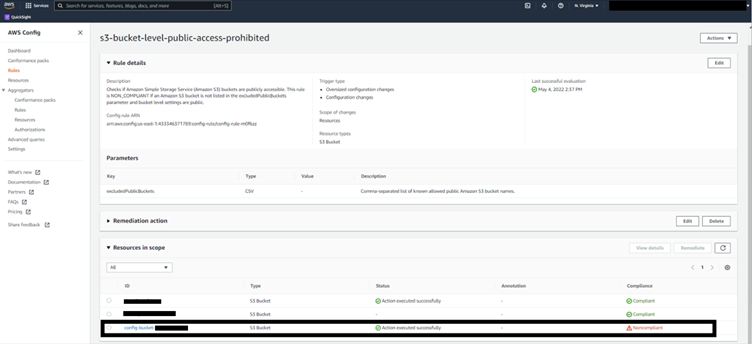
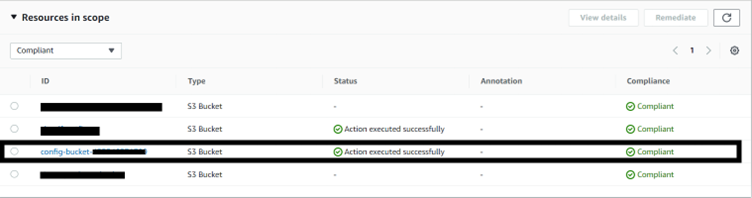
Continuous compliance is the continuous monitoring of IT assets to ensure compliance with regulatory security benchmarks. It continuously scans networks to detect risks in a non-stop approach.
Continuous compliance entails creating a culture and strategy within your organisation that constantly evaluates your compliance position to ensure you are meeting industry and regulatory requirements while maintaining secure systems.
In short, continuous compliance aims to shift IT teams away from reactively responding to audit requests and attacks and toward being proactive in their preparation for future threats and data reporting requirements.