Any organization that wants to stay ahead of the competition needs to have an effective DevOps program. DevOps has paved the way for faster software development and deployment while assuring complete customer satisfaction through the seamless integration of the Development and Operations teams. The DevOps culture has altered how IT operates by uniting teams to accomplish crucial business objectives. DevOps is built on automation and continual improvement. It’s a step in the direction of a release pipeline that is more reliable and consistent, as well as automation and improved communication.
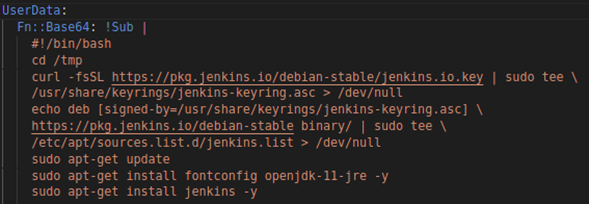
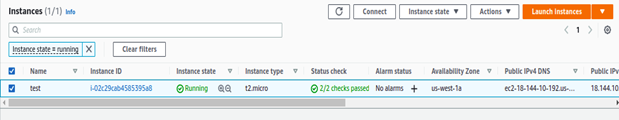
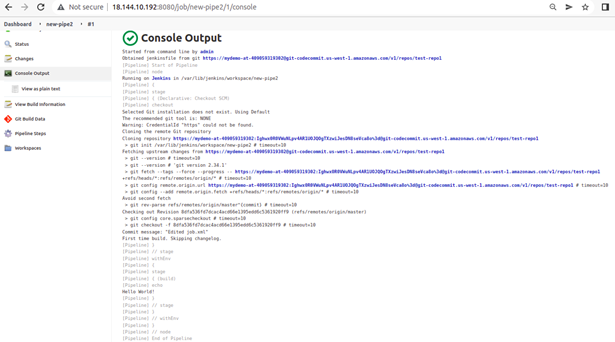
In Part 1 of this series, we have learned how applications can be installed, configured, and validated on AWS using Terraform. In this blog, we will use another IaC tool – CloudFormation, for the same purpose of targeting the Jenkins application.
It is unproductive to install and configure AWS resources manually. Additionally, it raises the possibility of configuration errors and inconsistencies, which can lead to problems and raise security risks. It also makes scaling or updating resources less effective.
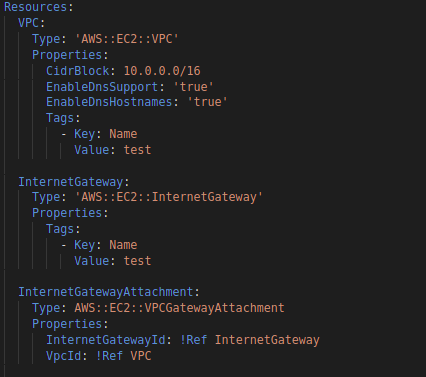
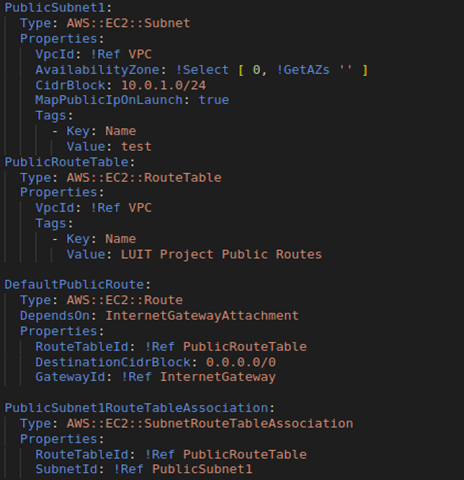
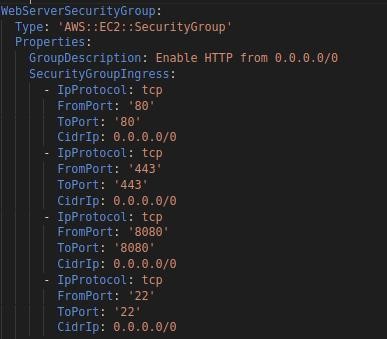
We can streamline the AWS deployment procedure by using an IaC tool like CloudFormation. Our resource configurations can be defined once, then deployed as many times as necessary.
Our CloudFormation templates allow us to keep track of how we configure our resources and how we have changed over time. We can also swiftly and predictably update resources using change sets.
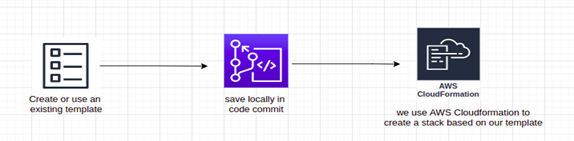
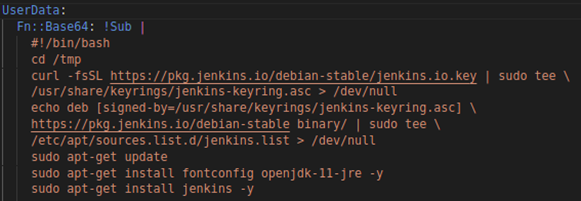
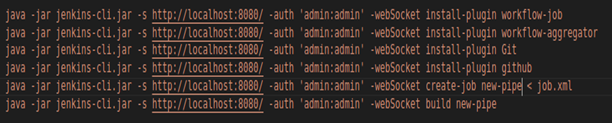
To have a completely scripted versioned architecture, we use CloudFormation. Everything, from the application to the virtual resources, is produced in the YAML script. As a result, we have total control over our AWS infrastructure and can be recreated whenever necessary.