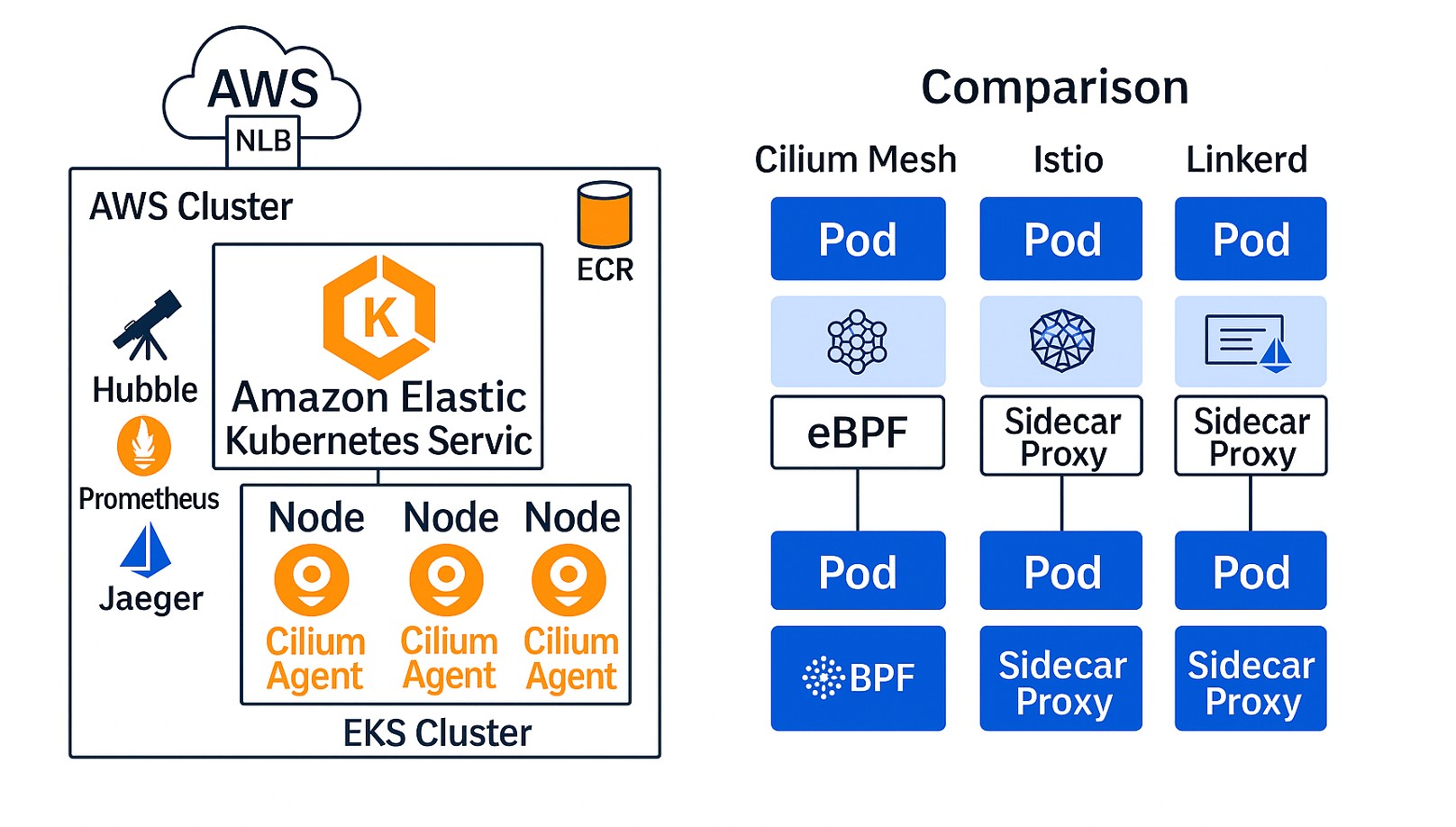
Kubernetes has become the go-to platform for deploying microservices, and with it comes the challenge of service communication, observability, and security. While traditional service meshes like Istio and Linkerd use sidecars to address these, Cilium Service Mesh brings a sidecar-less approach using eBPF, setting a new standard for performance and simplicity. This is a first-hand account of our journey implementing Cilium on AWS EKS, the challenges, the wins, and most importantly — why this could be a game-changer for your Kubernetes workloads.
What is Cilium & Why It’s Different?
Cilium is a modern service mesh and CNI (Container Network Interface) built on eBPF, a Linux kernel technology enabling highly performant and secure networking.
Unlike Istio or Linkerd, Cilium doesn’t rely on sidecar proxies — meaning:
- No resource-hungry sidecars
- Kernel-level observability & security
- Higher scalability and throughput
Our Experiences on deploying Cilium Mesh and achieved Goals
- Deploy Cilium Service Mesh on Amazon EKS
- Validate sidecar-less architecture
- Ensure real-time observability using Hubble
- Measure performance against Istio
- Integrate Prometheus & Jaeger
- Enable multi-cluster support